
This section describes the modeling of security control information in an OSCAL-based FedRAMP SSP. To ensure consistent processing, FedRAMP imposes specific requirements on the use of OSCAL for control implementation information.
The modeling of controls is addressed in the following sections as follows:

All control definition information is imported from the appropriate FedRAMP baseline (OSCAL profile). This includes the original NIST control definition and parameter labels as well as any FedRAMP control guidance and parameter constraints.
Interpreting and presenting profile content is out of the scope of this documentation. Please refer to the NIST OSCAL Profile and Catalog schema references for more information:
Only the control implementation information is present within an OSCAL-based SSP. Each control in the FedRAMP baseline must have a corresponding implemented-requirement assembly in the control-implementation assembly.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 href="https://path/to/xml/FedRAMP_MODERATE-baseline_profile.xml"/> This field required by OSCAL, but may be left blank. FedRAMP requires no specific content here. uuid="uuid-value" control-id="ac-1"> uuid="uuid-value" control-id="ac-2"> uuid="uuid-value" control-id="ac-2.1">
1 2 3 4 URI to Profile: /*/import-profile/@href CSP's Control Implementation Information /*/control-implementation/implemented-requirement[@control-id="ac-1"]NOTE: FedRAMP tools check to ensure there is one implemented-requirement assembly for each control identified in the applicable FedRAMP baseline.
Every applicable control must have at least one responsible-role defined. There must be a separate responsible-role assembly for each responsible role. OSCAL requires the specified role-id to be valid in the defined list of roles in the metadata . Controls with a FedRAMP implementation-status property value of “non-applicable” (see the Implementation Status section) do not require a responsible-role . FedRAMP further requires that the specified role-id must also have been referenced in the system-implementation user assembly. This equates to the FedRAMP requirement of all responsible roles appearing in the Personnel Roles and Privileges table.
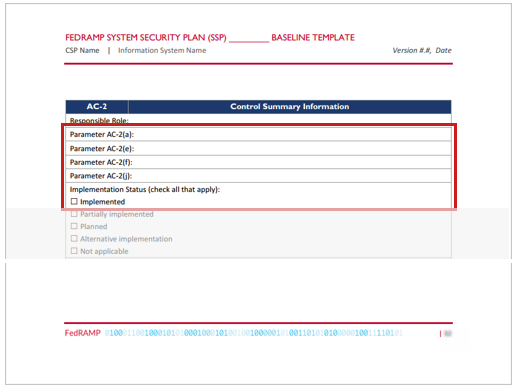
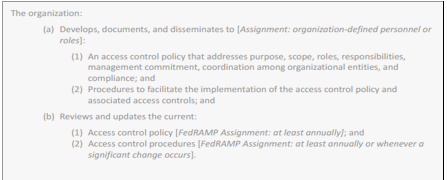
With the implemented-requirement assembly, there must be one set-parameter statement for each of the control’s parameters, as specified in the FedRAMP baseline and illustrated in the example representation below. The only exception to this is with nested parameters. Some select parameters contain an assignment parameter within a selection parameter, such as appears in AC-7 (b). In these instances, only the final selected value must be provided. The nested assignment parameter may be ignored.
OSCAL also supports parameter setting at the component level, within a by-component assembly.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 id="admin-unix"> Unix Administrator uuid="uuid-value"> admin-unix uuid="uuid-value" control-id="ac-2"> role-id="admin-unix" /> param-id="ac-2_prm_1"> System Manager, System Architect, ISSO
1 2 3 4 5 6 7 8 Number of specified Responsible Roles: count(/*/control-implementation/implemented-requirement[@control-id="ac-2"]/responsible-role) Responsible Role: /*/metadata/role[@id=/*/control-implementation/implemented-requirement[@control-id="ac-2"]/responsible-role[1]/@role-id]/title Check for existence in Personnel Roles and Privileges (Should return a number > 0) count(/*/system-implementation/user/role-id[string(.)=/*/control-implementation/implemented-requirement[@control-id="ac-2"]/responsible-role/@role-id]) Parameter Value: /*/control-implementation/implemented-requirement[@control-id="ac-2"]/set-parameter [@param-id="ac-2_prm_1"]/valueFedRAMP only accepts only one of five values for implementation-status : implemented, partial, planned, alternative, and not-applicable. A control may be marked “partial” and “planned” (using two separate implementation-status fields). All other choices are mutually exclusive.
If the implementation-status is partial, the gap must be explained in the remarks field.
If the implementation-status is planned, a brief description of the plan to address the gap, including major milestones must be explained in the remarks field. There must also be a prop (name="planned-completion-date" ns="https://fedramp.gov/ns/oscal") field containing the intended completion date. With XML, prop fields must appear before other sibling fields (such as set-parmeter , responsible-role , etc.), even though that sequence is counter-intuitive in this situation.
If the implementation-status is alternative, the alternative implementation must be summarized in the remarks field.
If the implementation-status is not-applicable, the N/A justification must be provided in the remarks field.
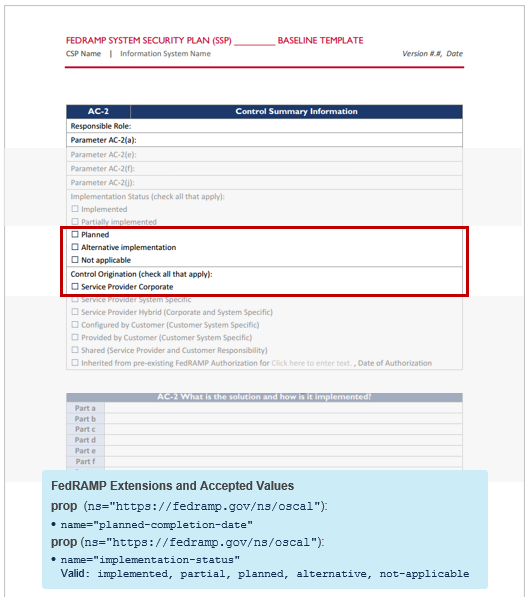
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 uuid="uuid-value" control-id="ac-1"> name="planned-completion-date" ns="https://fedramp.gov/ns/oscal" value="2021-01-01Z"/> name="implementation-status" ns="https://fedramp.gov/ns/oscal" value="implemented" /> name="implementation-status" ns="https://fedramp.gov/ns/oscal" value="partial" /> name="implementation-status" ns="https://fedramp.gov/ns/oscal" value="planned" /> name="implementation-status" ns="https://fedramp.gov/ns/oscal" value="not-applicable"/>
1 2 3 4 5 6 7 8 9 10 Implementation Status (may return more than 1 result for a given control) : /*/control-implementation/implemented-requirement[@control-id="ac-1"] /prop[@name="implementation-status"]/@value Gap Description (If implementation-status="partial"): /*/control-implementation/implemented-requirement/prop[@name='implementation-status'][@value="partial"][@ns="https://fedramp.gov/ns/oscal"]/remarks/node() Planned Completion Date (If implementation-status="planned"): /*/control-implementation/implemented-requirement[@control-id="ac-1"]/prop[@name="planned-completion-date"][@ns="https://fedramp.gov/ns/oscal"]/@value Plan for Completion (If implementation-status="planned"): /*/control-implementation/implemented-requirement/prop[@name='implementation-status'][@value="planned"][@ns="https://fedramp.gov/ns/oscal"]/remarks/node() Not Applicable (N/A) Justification (If implementation-status="na"): /*/control-implementation/implemented-requirement/prop[@name='implementation-status'][@value="not-applicable"][@ns="https://fedramp.gov/ns/oscal"]/remarks/node()The FedRAMP implementation-status property at the control’s implemented-requirement level is a summary of all statement and/or component level core OSCAL implementation-status designations. It must be set appropriately based on the least value of child statement or component level implementation-status designations. When a statement and/or component level implementation-status designation is not specified, the FedRAMP implementation-status value is assumed. Individual statements and/or components may override implementation-status locally.
FedRAMP accepts only one of five values for control-origination : sp-corporate, sp-system, customer-configured, customer-provided, and inherited. Hybrid choices are expressed by identifying more than one control-origination , each in a separate prop field.
For controls with a control-id ending in "-1", FedRAMP only accepts sp-corporate and sp-system.
If the control origination is inherited, there must also be a FedRAMP extension (prop name="leveraged-authorization-uuid" ns="https://fedramp.gov/ns/oscal") field containing the UUID of the leveraged authorization as it appears in the /*/system-implementation/leveraged-authorization assembly.

1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 uuid="uuid-of-leveraged-authorization"> uuid="uuid-value" control-id="ac-2"> name="leveraged-authorization-uuid" value="uuid-of-leveraged-authorization"/> ns="https://fedramp.gov/ns/oscal" name="control-origination" value="sp-corporate" /> ns="https://fedramp.gov/ns/oscal" name="control-origination" value="sp-system" /> ns="https://fedramp.gov/ns/oscal" name="control-origination" value="customer-configured" /> ns="https://fedramp.gov/ns/oscal" name="control-origination" value="inherited" />
1 2 3 4 5 6 7 8 Number of Control Originations: count(/*/control-implementation/implemented-requirement[@control-id="ac-2"]/prop[@name="control-origination"][@ns="https://fedramp.gov/ns/oscal"]) Control Origination(could return more than 1 result): /*/control-implementation/implemented-requirement[@control-id="ac-2"]/prop[@name="control-origination"][@ns="https://fedramp.gov/ns/oscal"][1]/@value Inherited From: System Name (If control-origination="inherited"): /*/system-implementation/leveraged-authorization[@uuid=/*/control-implementation/implemented-requirement[@control-id="ac-2"]/prop[@name="leveraged-authorization-uuid"]]/title Inherited From: Authorization Date (If control-origination="inherited"): /*/system-implementation/leveraged-authorization[@uuid=/*/control-implementation/implemented-requirement[@control-id="ac-2"]/prop[@name="leveraged-authorization-uuid"]]/date-authorized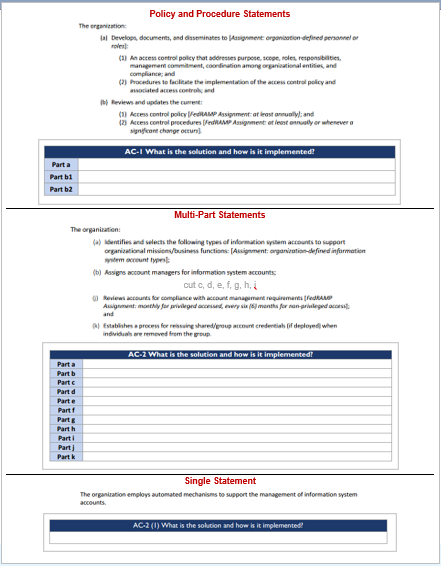
Within the OSCAL-based FedRAMP baselines, control statements and control objectives are tagged with a response-point FedRAMP Extension. Every control statement designated as a response-point in the baseline must have a statement with the control’s implemented-requirement assembly. Please note that control objective response points are used for the SAP and SAR.
When using a FedRAMP Resolved Profile Catalog, the following query will identify the response points for a given control.
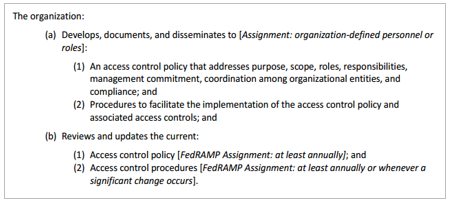
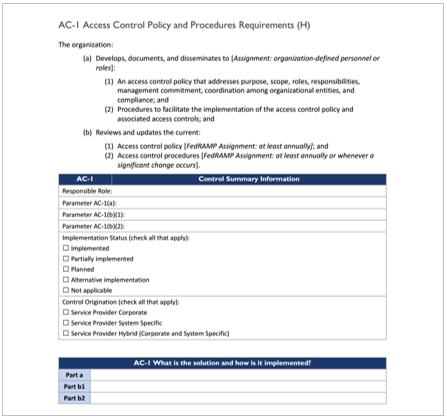
Response Points for AC-1: //control[@id='ac-1']/part[@name='statement']//prop[@name='response-point'][@ns='https://fedramp.gov/ns/oscal']/../@idFor each of the -1 controls, such as AC-1, there must be exactly four statement assemblies: Part (a)(1), Part (a)(2), Part (b)(1), and Part (b)(2).
1 2 3 4 5 6 7 8 9 10 uuid="uuid-value" control-id="ac-1"> statement-id="ac-1_smt.a.1"> statement-id="ac-1_smt.a.2"> statement-id="ac-1_smt.b.1"> statement-id="ac-1_smt.b.2"> There must be one statement assembly for each lettered part, such as with AC-2, parts a, b, c, etc.
1 2 3 4 5 6 7 8 9 uuid="uuid-value" control-id="ac-2"> statement-id="ac-2_smt.a"> statement-id="ac-2_smt.k"> If there are no lettered parts in the control definition, such as with AC-2 (1), there must be exactly one statement assembly.
1 2 3 4 5 6 7 control-id="ac-2.1"> statement-id="ac-2.1_smt"> Within each statement assembly, all responses must be provided within one or more by-component assemblies. There must always be a component defined in the system-implementation representing the system as a whole (“THIS SYSTEM”), even if individual components are defined that comprise the system. See the Working with Components section for more information.
An OSCAL-based FedRAMP SSP should define individual components of the system. Components are not just hardware and software. Policies, processes, FIPS 140 validation information, interconnections, services, and underlying systems (leveraged authorizations) are all components.
With OSCAL, the content in the cell next to Part a must be broken down into its individual components and responded to separately.
The following are examples.
Within each of the statement assemblies, all responses appear in one or more by-component assemblies. Each by-component assembly references a component defined in the system-implementation assembly.

1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 uuid="uuid-value" type="software"> Component Title Description of the component. state="operational"/> uuid="uuid-value" type="process"> Process Title Description of the component. state="operational"/> role-id="admin-unix"> 3360e343-9860-4bda-9dfc-ff427c3dfab6 uuid="uuid-value" control-id="ac-2"> uuid="uuid-value" statement-id="ac-2_smt.a"> uuid="uuid-value" component-uuid="uuid-of-software-component"> Describe how the software component is satisfying the control. uuid="uuid-value" component-uuid="uuid-of-process-component"> Describe how the process satisfies the control.
NOTES:
There must always be a “This System” component in the SSP. This is used in several ways:

1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 uuid="uuid-value" type="this-system"> This System Description of the component. state="operational"/> uuid="uuid-value" control-id="ac-2"> uuid="uuid-value" statement-id="ac-2_smt.a"> uuid="uuid-value" component-uuid="uuid-of-this-system-component"> Describe how individual components are working together. Describe how the system - as a whole - is satisfying this statement. This can include policy, procedures, hardware, software, etc.
NOTES:
Any time policies, procedures, plans, and similar documentation are cited in a control response, they must be linked.
For the legacy approach, when responding within the by-component assembly for “this system”, the link must be within the same by-component assembly where the artifact is cited.
1 2 3 4 5 6 7 8 9 10 11 12 13 uuid="uuid-value" control-id="ac-1"> uuid="uuid-value" statement-id="ac-1_smt.a"> component-uuid="uuid-of-this-system" uuid="uuid-value"> Describe how Part a is satisfied within the system. href="#uuid-of-policy-resource-in-back-matter" rel="policy" />
For the component approach, use the component representing the policy. The link should be in the component, but may be added directly to the by-component as well.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 uuid="uuid-value" type="policy"> Access Control and Identity Management Policy An example component representing a policy. href="#uuid-of-policy-resource-in-back-matter" rel="policy" /> state="operational"/> uuid="uuid-value" control-id="ac-1"> uuid="uuid-value" statement-id="ac-1_smt.a"> component-uuid="uuid-of-policy-component" uuid="uuid-value"> Describe how this policy satisfies Part a.
For either example above, the policy must be present as a resource in back-matter .
1 2 3 4 5 6 7 uuid="uuid-value"> Access Control and Identity Management Policy media-type="application/pdf" href="./documents/policies/sample_policy.pdf" /> filename="sample_policy.pdf" media-type="application/pdf">00000000 For systems that may be leveraged, OSCAL enables a robust mechanism for providing both inheritance details as well as customer responsibilities (referred to as consumer responsibilities by NIST). OSCAL is designed to enable leveraged and leveraging system SSP details to be linked by tools for validation.
Within the appropriate by-component assembly, include an export assembly. Use provided to identify a capability that may be inherited by a leveraging system. Use responsibility to identify a customer responsibility . If a responsibility must be satisfied to achieve inheritance, add the provided-uuid flag to the responsibility field.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 uuid="uuid-value" control-id="ac-2"> uuid="uuid-value" statement-id="ac-2_smt.a"> uuid="uuid-value" component-uuid="uuid-of-this-system-component"> Describe how the system - as a whole - is satisfying this statement. uuid="uuid-value"> Leveraging system's responsibilities in satisfaction of AC-2. Not linked to inheritance, so this is always required. role-id="customer" /> uuid="uuid-value" component-uuid="uuid-of-software-component"> Describe how the software is satisfying this statement. uuid="uuid-value"> Customer appropriate description of what may be inherited. role-id="poc-for-customers" /> uuid="uuid-value" provided-uuid="uuid-of-provided"> Customer responsibilities if inheriting this capability. role-id="customer" /> When the current system is inheriting a control from or meeting customer responsibilities defined by an underlying authorization, the leveraged system must first be defined as described in the Response: Identifying Inheritable Controls and Customer Responsibilities section, and documented a component int the leveraging system SSP before it may be referenced in a control response. The by-component assembly references these components.
IMPORTANT: The leveraged system may provide a single component representing the entire leveraged system
or may provide individual system components as well. In either case, the inherited-uuid property in the component must have the value flag set to the UUID of the leveraged system or component.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 uuid="uuid-value" type="this-system"> uuid="uuid-value" type="leveraged-system"> LEVERAGED SYSTEM as a whole (IaaS) name="leveraged-authorization-uuid" value="uuid-of-LA-in-this-SSP" /> name="inherited-uuid" value="uuid-of-component-in-leveraged-SSP" /> uuid="uuid-value" type="service"> Service Provided by Leveraged System name="leveraged-authorization-uuid" value="uuid-of-LA-in-this-SSP" /> name="inherited-uuid" value="uuid-of-component-in-leveraged-SSP" /> uuid="uuid-value" control-id="ac-2"> uuid="uuid-value" statement-id="ac-2_smt.a"> uuid="uuid-value" component-uuid="uuid-of-this-system-component"> Describe what is satisfied by this system. uuid="uuid-value" component-uuid="uuid-leveraged-system-component"> Describe what is inherited from the leveraged system in satisfaction of this control statement. provided-uuid="uuid-of-provided" uuid="uuid-value"> Optional: Information provided by leveraged system. responsibility-uuid="uuid-of-responsibility" uuid="uuid-value" > Description of how the responsibility was satisfied.
Use the following XPath queries to retrieve basic control response information. For any given control response part, tools should list the name of each component cited by a by-component assembly, as well as the description.

1 2 3 4 5 6 7 8 9 10 Number of cited components for AC-2, part a (Integer): count(/*/control-implementation/implemented-requirement[@control-id="ac-2"]/statement[@statement-id="ac-2_smt.a"]/by-component) Name of first component related to AC-2, part a: /*/system-implementation/component[@uuid=/*/control-implementation/implemented-requirement[@control-id="ac-2"]/statement[@statement-id="ac-2_smt.a"]/by-component[1]/@component-uuid]/title "What is the solution and how is it implemented?" for AC-2, Part (a), first component: /*/control-implementation/implemented-requirement[@control-id="ac-2"]/statement[@statement-id="ac-2_smt.a"]/by-component[1]/description/node() Is there a customer responsibility for the first component in AC-2, part a? (true/false): boolean(/*/control-implementation/implemented-requirement[@control-id="ac-2"]/statement[@statement-id="ac-2_smt.a"]/by-component[1] /prop[@name='responsibility'][@value='customer']) Customer responsibility statement for the first component in AC-2, part a: /*/control-implementation/implemented-requirement[@control-id="ac-2"]/statement[@statement-id="ac-2_smt.a"]/by-component[1]/prop[@name='responsibility'][@value='customer']/remarks/node() NOTES:
This page was last updated on July 17, 2024. Improve this Page.